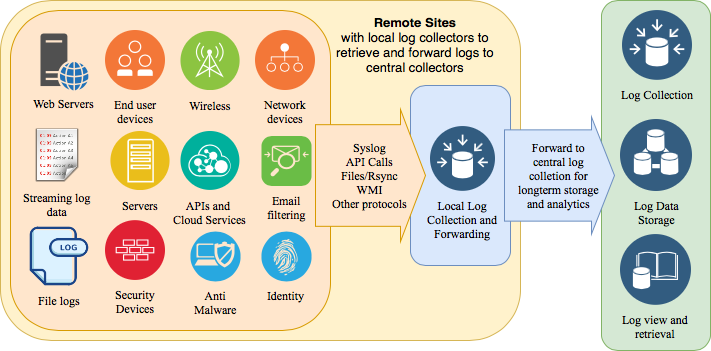
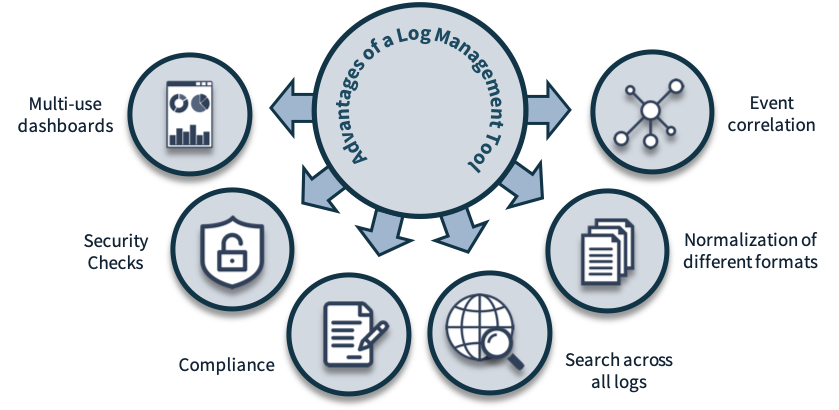
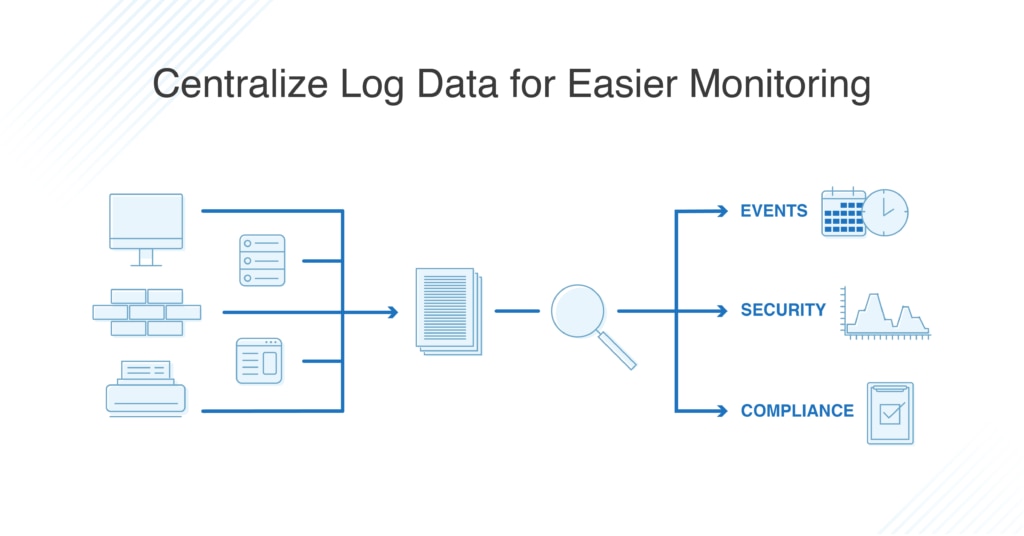
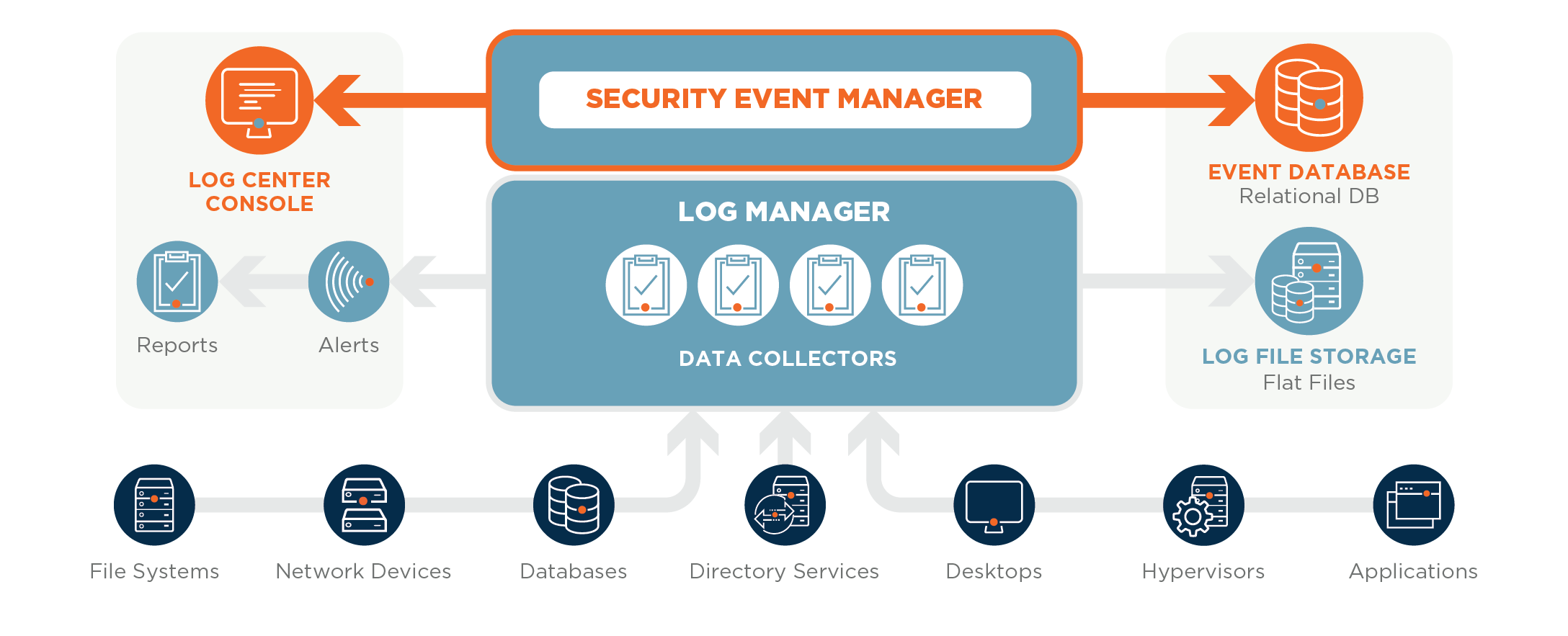
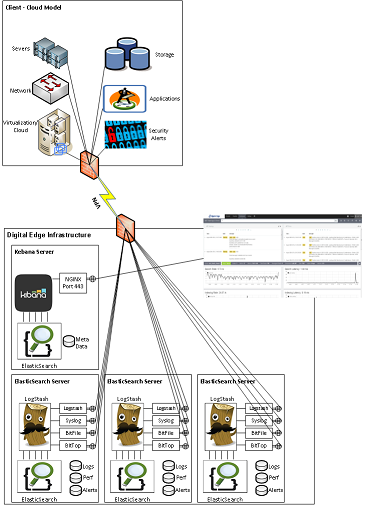
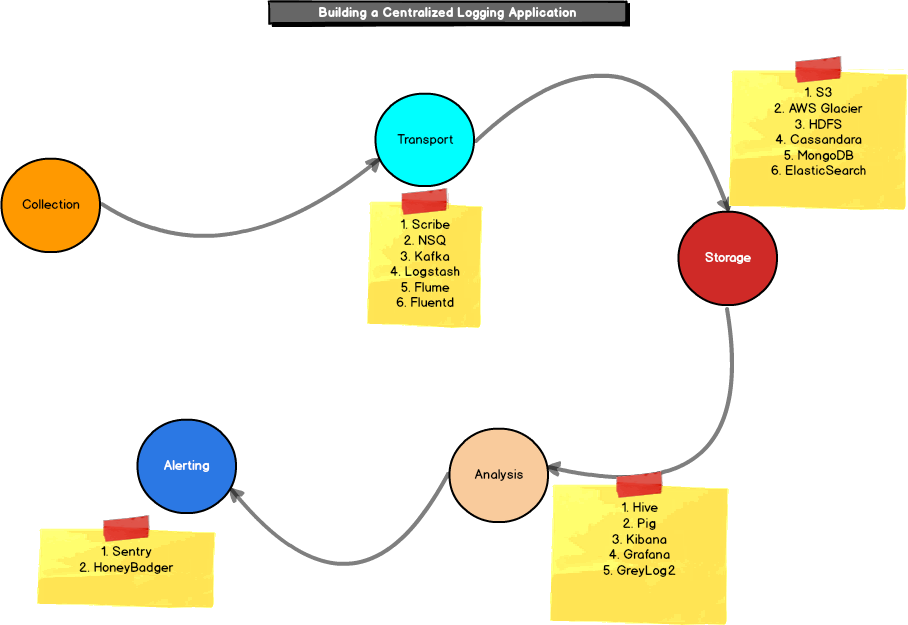
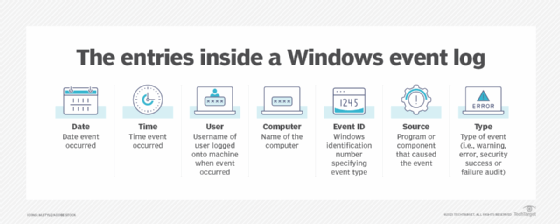
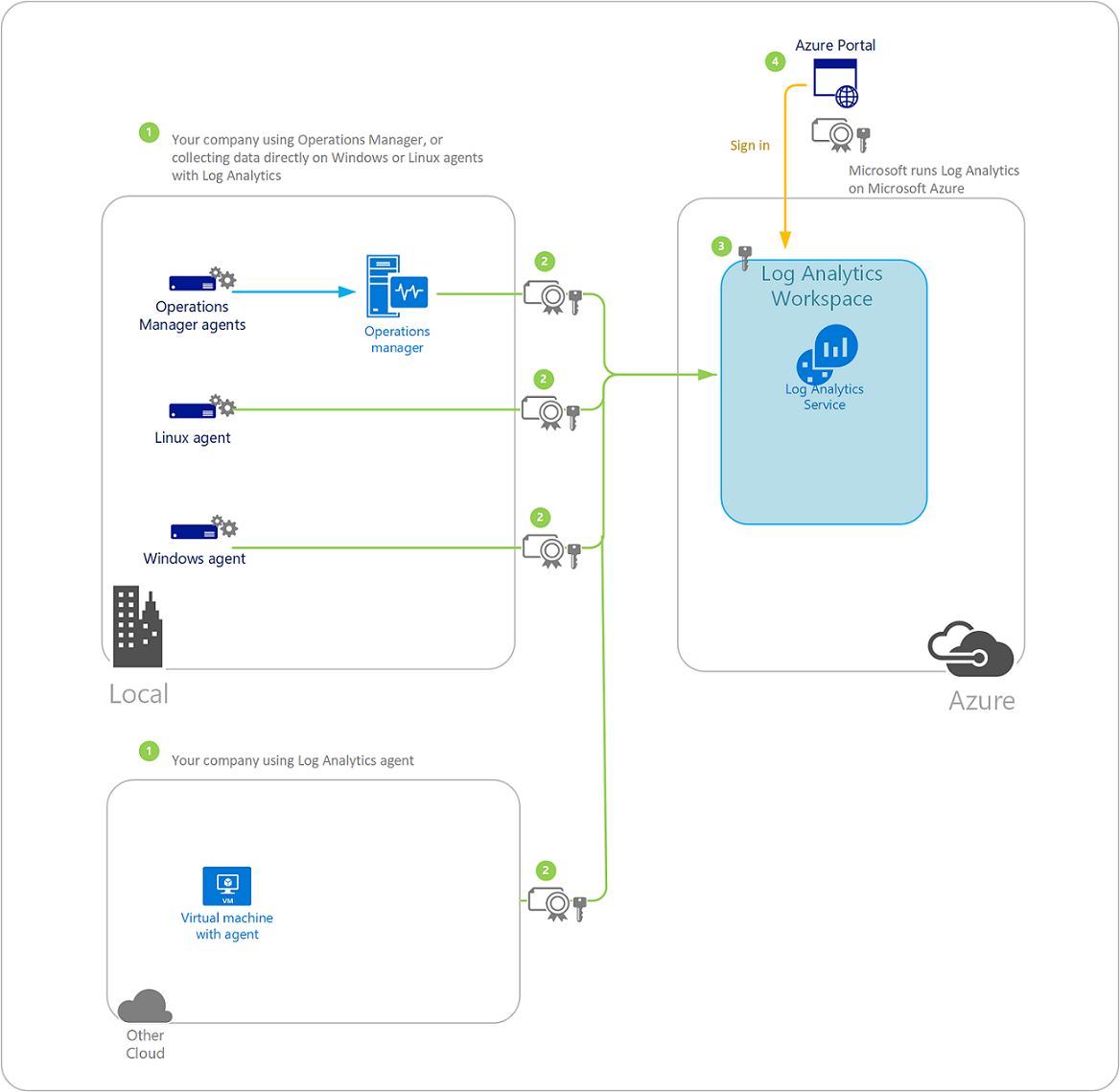
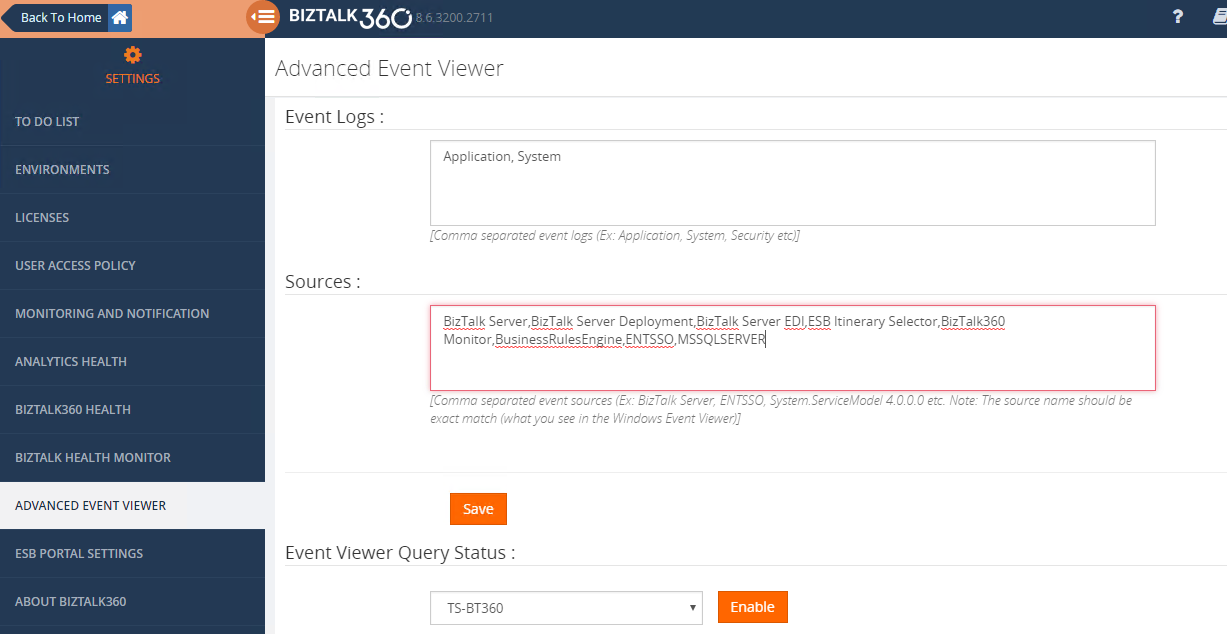
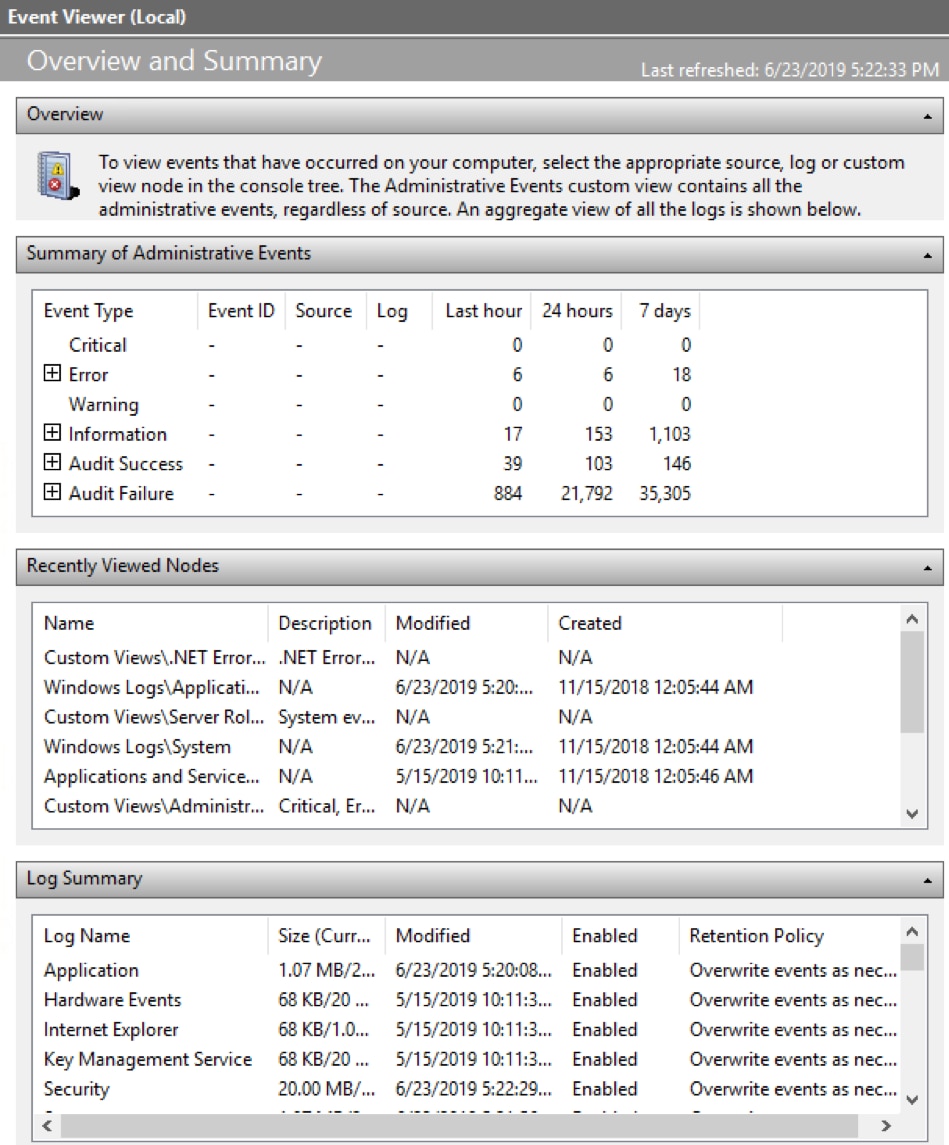
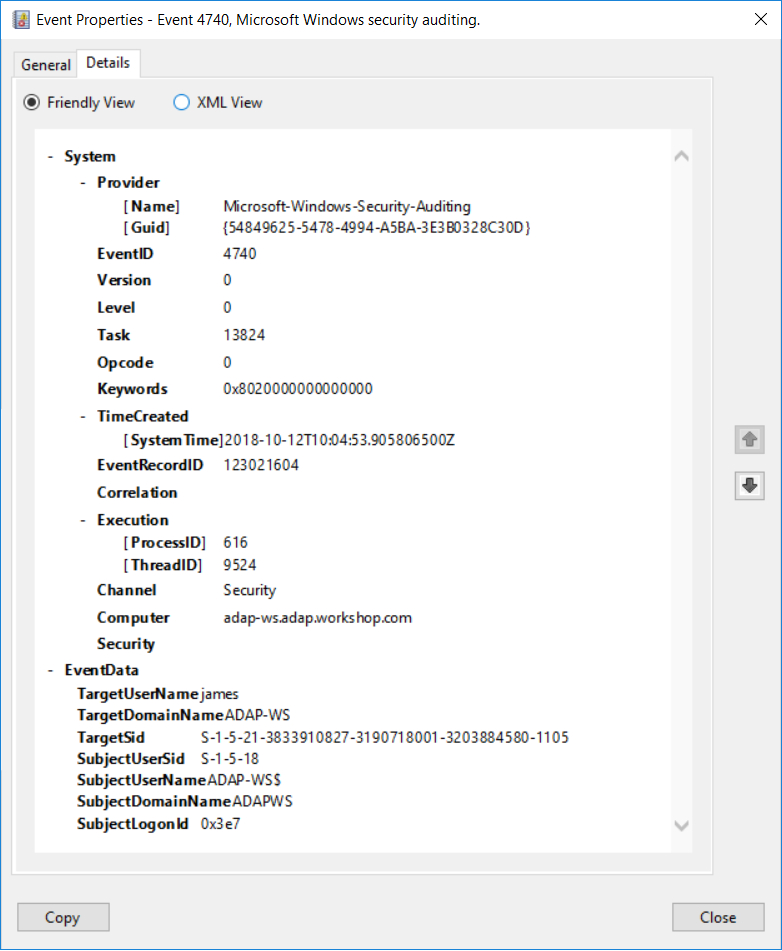
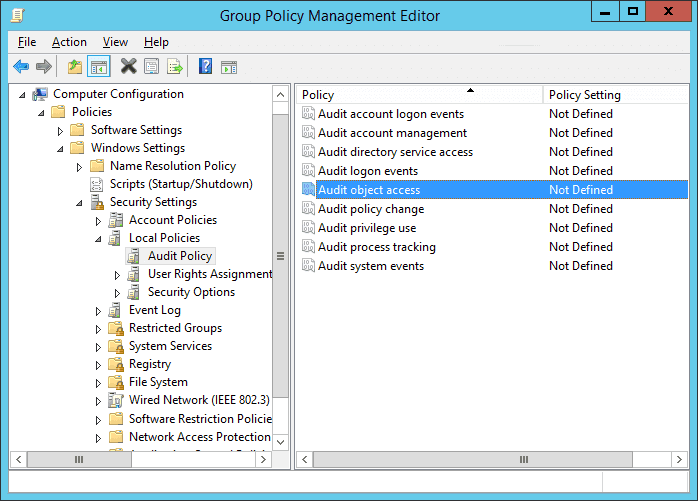
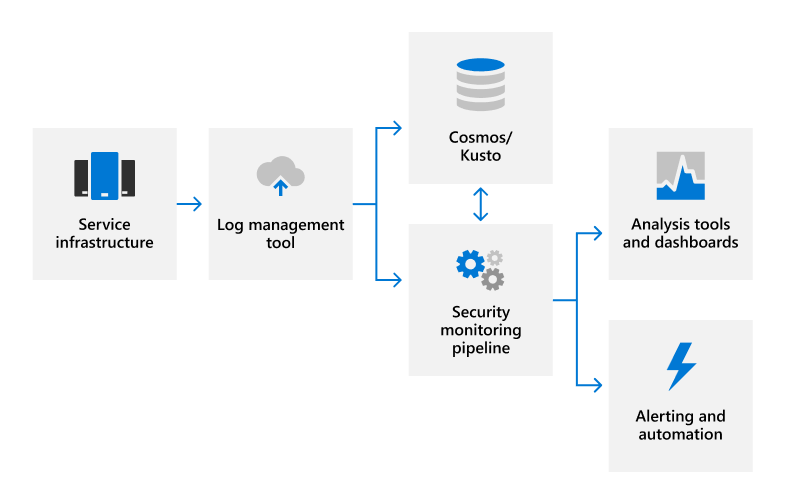
Section 7 – Mitigate threats using Microsoft Defender for Cloud – Plan and implement the use of data connectors for ingestion of data sources in Microsoft Defender for Cloud – Set-AzWebApp -name "

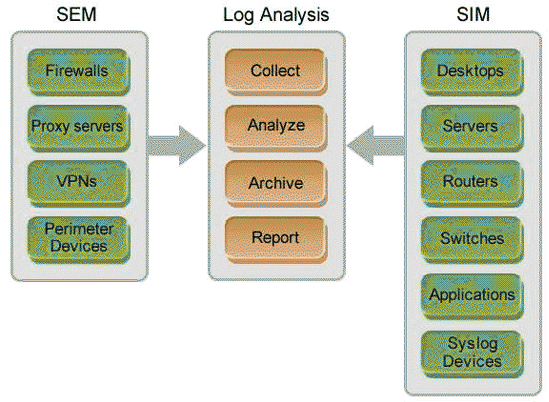
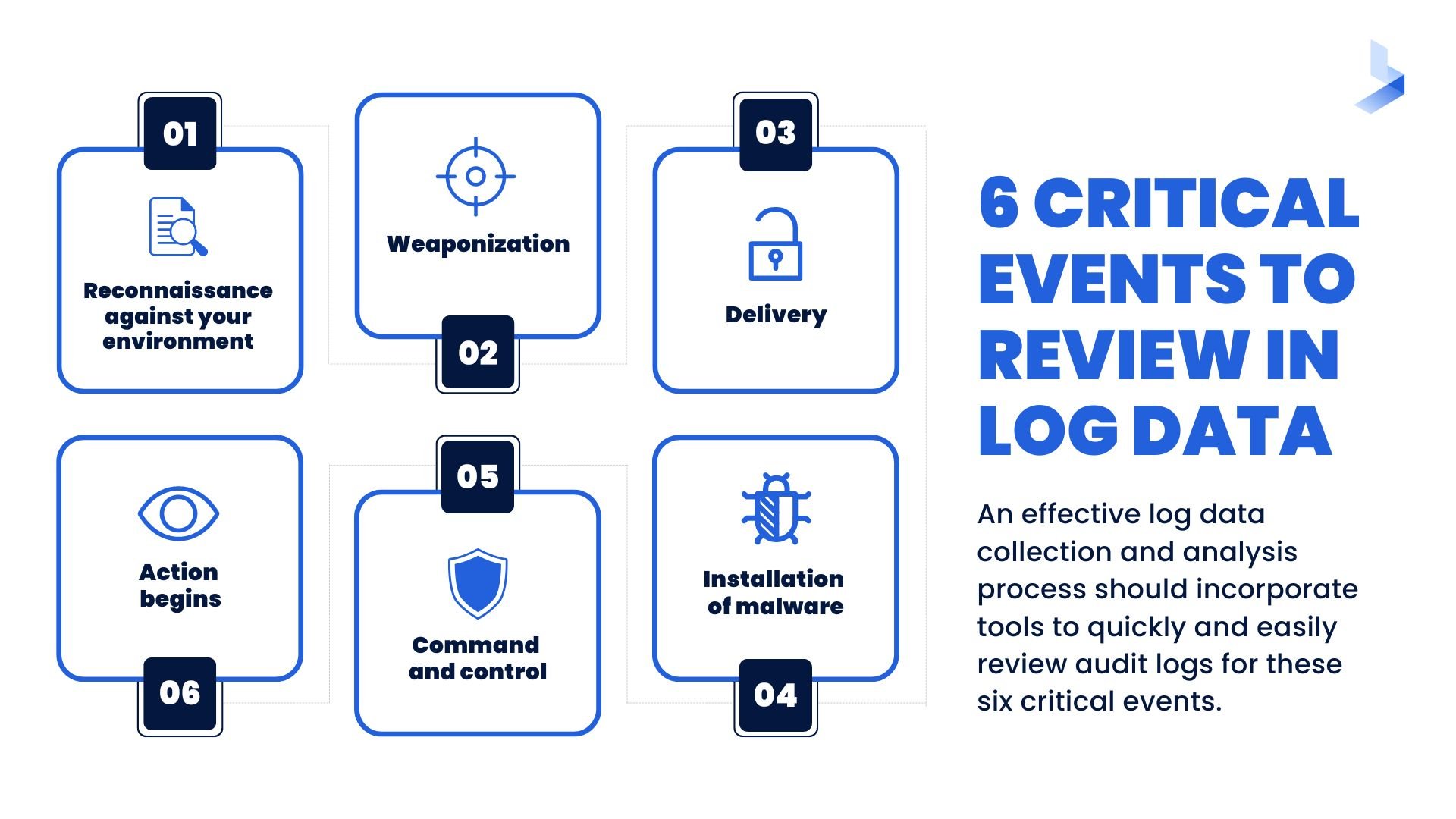
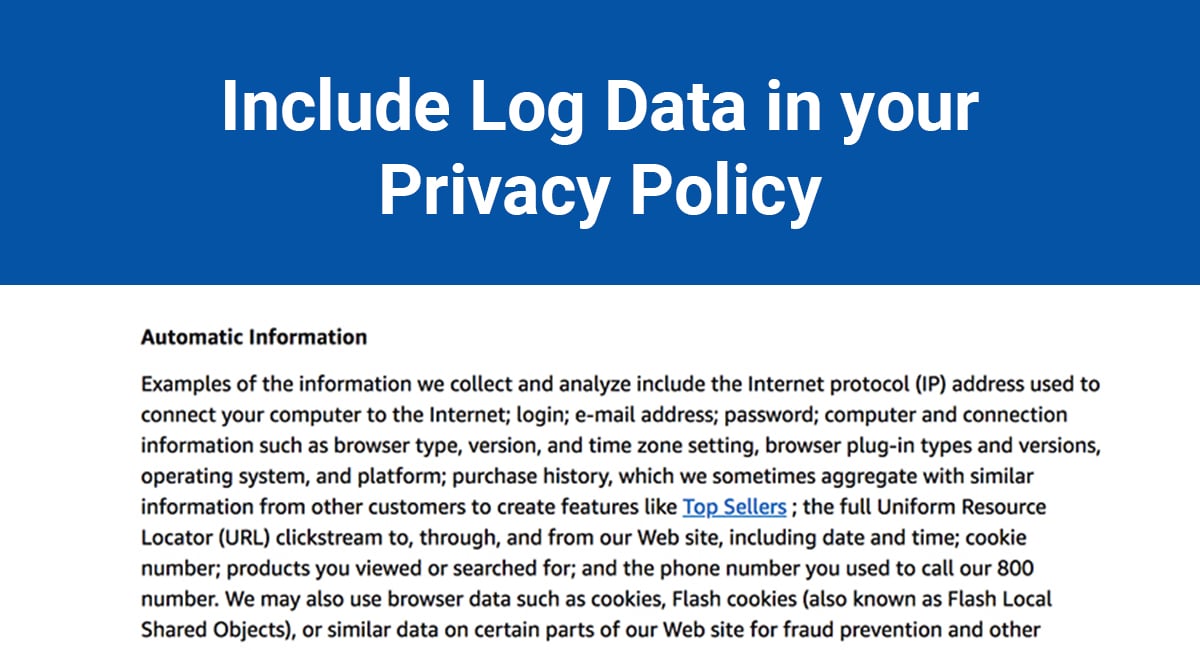
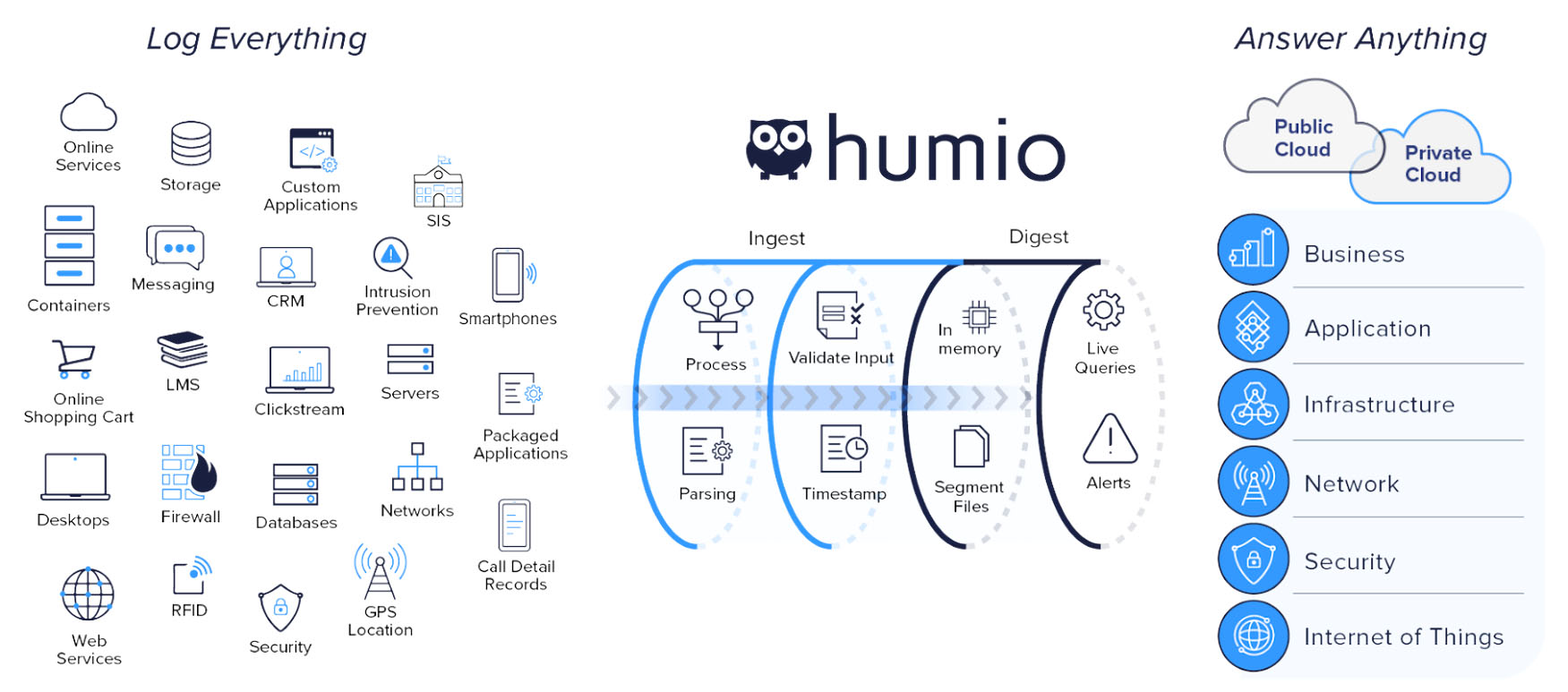
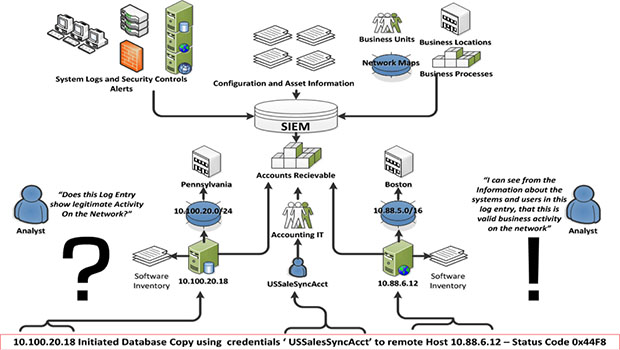
What Is Security Information and Event Management (SIEM)? Definition, Architecture, Operational Process, and Best Practices - Spiceworks