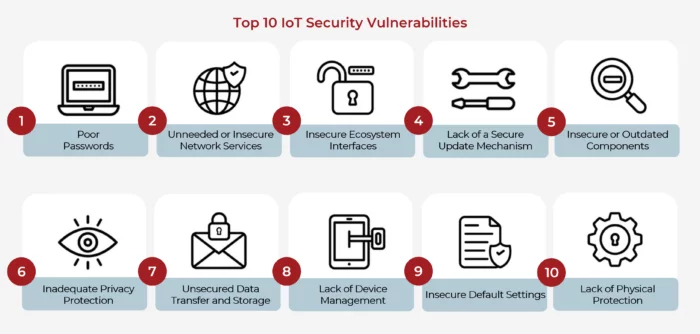
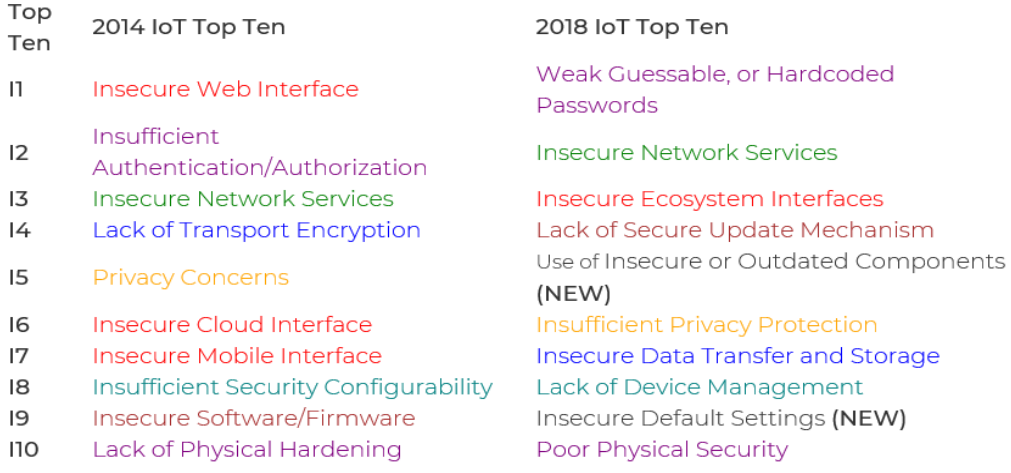
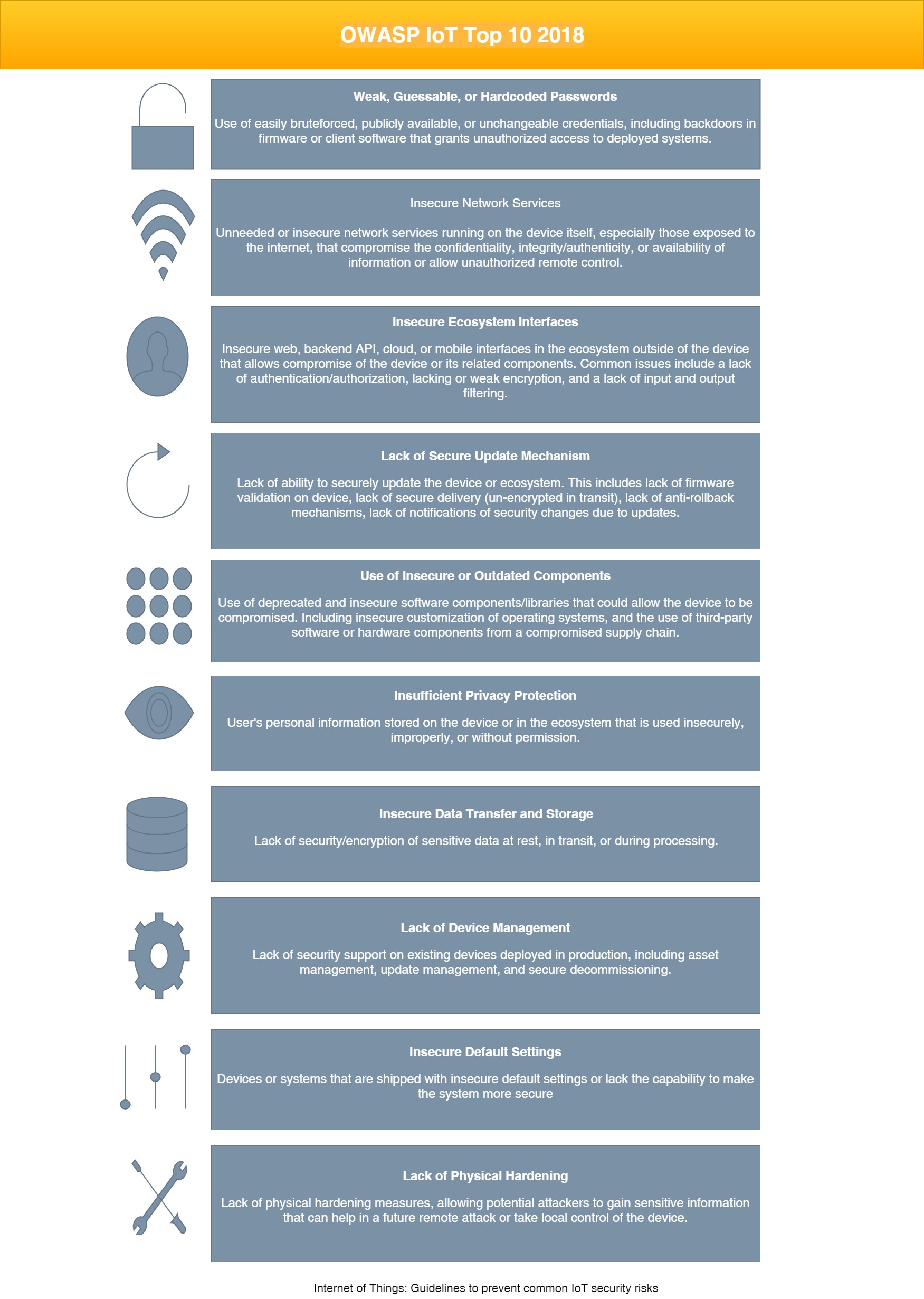
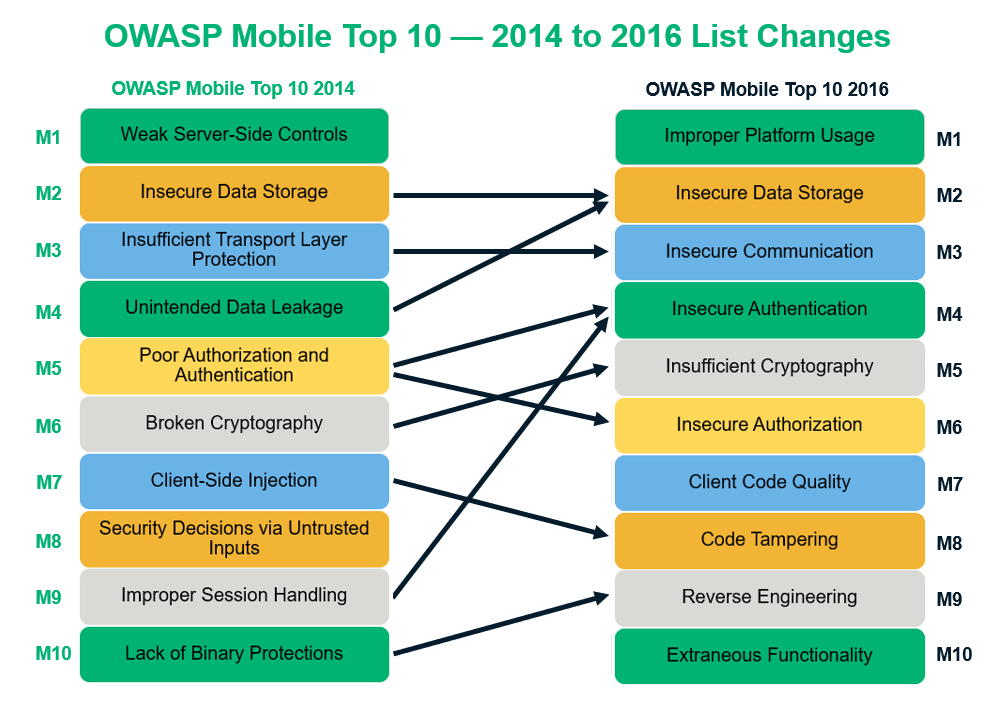
Cigdem Sengul on Twitter: "Tried to map how OWASP advice on Top 10 things to avoid in #IoT changed from 2014 to 2018. Linked intuitively but other constellations possible (link weight indicative
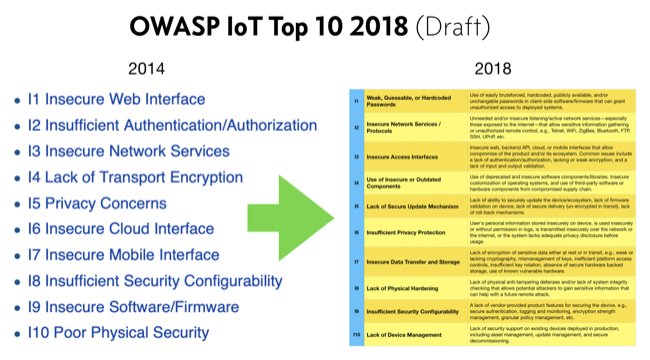
Neira Jones on Twitter: "Preparing to Release the #OWASP #IoT Top 10 2018 https://t.co/cCSmVTmtBB #infosec #appsec #DevSecOps @owasp https://t.co/2WaPcvn4A5" / Twitter